GTP - Web Penetration Testing Service Provider
We Can Show You What Hackers See In Your Website and How They Can Hack It!
-

Authentication
-

Authorization
-

Session Management
-
Data Validation
-

Buffer Overflows
At GTP we think like hackers and act professional. Our expertise is acknowledged by industry experts. Our certified security experts are fully equipped to address your web application penetration testing needs.
Web Application Risk
Over 80% of all compromises are the result of exploited web application vulnerabilities. In many cases the vulnerabilities that result in compromise are entirely missed by conventional testing methodologies (especially methodologies that are dependent on automation). In other cases vulnerabilities are identified but are incorrectly assumed to be non-exploitable due to coding standards and / or protective technologies. For example, a common misconception is that one can use parametrized queries to eliminate all sql injection vulnerabilities. The truth is that if the parametrized queries are not constructed properly then exploitation is often still possible. Another misconception is that Web Application Firewalls protect web applications from attack. The truth is that Web Application Firewalls only defend against attacks that they are programmed to detect but are ineffective at protecting against new attack methodologies.
How Web Application Penetration Testing Works?
- Penetration test start with the agreement of the scope. Once the scope is agreed then White hat hackers from our SOC will test your web application for vulnerabilities.
- All identified vulnerabilities are captured during this phase and used as an input for further investigation.
- Using the vulnerabilities identified in the web interface our testers will try to circumvent your perimeter security and test the effectiveness of controls put in place for on your web application infrastructure.
- We will always remain in our scope and will be extra vigilant to ensure we do not compromise the confidentiality and integrity of your data.
- The final report will include screenshots of hacked areas and identified findings along with its importance (severity) in compromising your environment.
We are not just another penetration testing company. We have our proprietary Vulnerability Management that enables us to find more web application security flaws. We Deliver a lots of Penetration Testing Projects by providing our best work to them.
How We Are Different From Others?
Our security professionals receive better training and have significant application development experience, which is important because web services are essentially programmatic interfaces that are best understood by people with a strong software development background. We have experience testing every major type of web service, including SOAP, REST, and custom protocols, and can work with any form of authentication, from OAUTH tokens to client certificates to custom digital signatures.
Step-By-Step Approach To Web Application Security
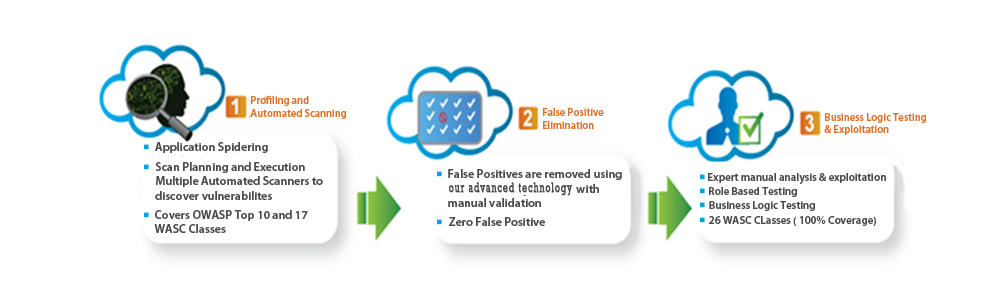
Application security testing and analysis follows a structured process of steps, each of which provides the tester with additional knowledge of the application structure. This is necessary to identify and conclusively validate the existence of a specific vulnerability, thereby eliminating false positives. The process begins with host and service enumeration. After that, content enumeration and discovery. A web crawl of application and associated servers follows. Finally, the testing of user-accepted input sources is performed, concluding with the testing of login forms and credentials, and the examination of session cookies used by the application.
- To execute a real-world attack on a critical application and understand the level of risk that exists at a single moment in time.
- To complement your automated scanning appliance to better identify and validate all security vulnerabilities.
- To understand how well your development team followed
the secure software development life cycle.
Why perform Web Apps Security Testing?
- Provide management with an understanding of the level of risk introduced by the web application.
- Provide recommendations and details to facilitate a cost-effective and targeted mitigation approach.
- Create a basis for future decisions regarding information security strategy and resource allocation.
The Goals of Web App Security Testing:
Website security breach can put you in a difficult situation So Let's Try Our Advanced Security Testing Services
Top 10 Open Web Application Security Project (OWASP)
- 1
Injection
- 2
Cross-Site Scripting (XSS)
- 3
Broken Authentication and Session Management
- 4
Insecure Direct Object Reference
- 5
Cross-Site Request Forgery (CSRF)
- 6
Security Misconfiguration
- 7
Insecure Cryptographic Storage
- 8
Failure to Restrict URL Access
- 9
Insufficient Transport Layer Protection
- 10
Unvalidated Redirects and Forwards


